National Security Agency: The Empire's central nervous system
systematic surveillance did not start (or end) with Bush II
the government is listening to the people
related page: NSA during 9/11 - nuclear warning systems did not alert Bush
- world's largest electronic vacuum cleaner
- NSA whistleblower Russel Tice: wiretapping Obama - June 19, 2013
- The Puzzle Palace
- Post Constitutional America
- yottabyte data centers
- motives for domestic spying
- NSA Charter, 1952
- Echelon - Five Eyes: US, UK, Canada, Australia, New Zealand
- Stasi on steroids
- NSA - GCHQ wind farm
- PRISM & Room 641A
- Church committee
NSA Headquarters: world's largest collection of computers |
Fourth Amendment, United States Constitution The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized. |
 update June 2013: The revelations that the NSA is tapped directly into the largest internet companies (Microsoft, Yahoo, Google, Apple, etc.) is not really a surprise. Did anyone really think the internet was not bugged?
update June 2013: The revelations that the NSA is tapped directly into the largest internet companies (Microsoft, Yahoo, Google, Apple, etc.) is not really a surprise. Did anyone really think the internet was not bugged?
- search topics: PRISM, Boundless Informant, Room 641A, Utah Data Center, Texas Cryptology Center, Stellar Wind, The Program, Shamrock, Minaret, Church Committee, Narus Insight Intercept Suite, Main Core, Five Eyes, Echelon, UKUSA Agreement, Foreign Intelligence Surveillance Court, Central Security Service, Panopticon
- whistleblowers: Mark Klein, William Binney, Thomas Drake, Russell Tice, Edward Snowden
- authors: James Bamford ("The Puzzle Palace," "Body of Secrets," "A Pretext for War," "The Shadow Factory"), Jeffrey Richelson ("The US Intelligence Community"), Tim Shorrock ("Spies for Hire: The Secret World of Outsourced Intelligence"), William Burrows, "Deep Black: Space Espionage and National Security"
Every breath you take Every single day |
|
 "The king hath note of all that they intend. By interception which they
dream not of."
"The king hath note of all that they intend. By interception which they
dream not of."
-- Henry V (Shakespeare)
Any sound that Winston made, above the level of a very low whisper, would be picked up by it, moreover, so long as he remained within the field of vision which the metal plaque commanded, he could be seen as well as heard. There was of course no way of knowing whether you were being watched at any given moment. How often, or on what system, the Thought Police plugged in on any individual wire was guesswork. It was even conceivable that they watched everybody all the time. But at any rate they could plug in your wire whenever they wanted to. You had to live -- did live, from habit that became instinct -- in the assumption that every sound you made was overheard, and, except in darkness, every movement scrutinized.
-- "Nineteen Eighty Four," by George Orwell
 "that [surveillance] capability at any time could
be turned around on the American people and no American would have any privacy
left, such [is] the capability to monitor everything: telephone conversations,
telegrams, it doesn't matter. There would be no place to hide. If this
government ever became a tyranny, if a dictator ever
took charge in this country, the technological capacity that the intelligence
community has given the government could enable it to impose total tyranny,
and there would be no way to fight back, because the most careful effort to
combine together in resistance to the government, no matter how privately it
was done, is within the reach of the government to know. Such is the
capability of this technology ...
"that [surveillance] capability at any time could
be turned around on the American people and no American would have any privacy
left, such [is] the capability to monitor everything: telephone conversations,
telegrams, it doesn't matter. There would be no place to hide. If this
government ever became a tyranny, if a dictator ever
took charge in this country, the technological capacity that the intelligence
community has given the government could enable it to impose total tyranny,
and there would be no way to fight back, because the most careful effort to
combine together in resistance to the government, no matter how privately it
was done, is within the reach of the government to know. Such is the
capability of this technology ...
"I don't want to see this country ever go across the bridge. I
know the capacity that is there to make tyranny total in America, and we must
see to it that this agency [NSA] and all agencies that possess this technology
operate within the law and under proper supervision, so that we never
cross over that abyss. That is the abyss from which there is no return."
-- Senator Frank Church (D-Idaho), 1975
By using the NSA to spy on American citizens, Binney told me, the United States has created a police state with few parallels in history: "It's better than anything that the KGB, the Stasi, or the Gestapo and SS ever had." He compared the situation to the Weimar Republic, a brief period of liberal democracy that preceded the Nazi takeover of Germany. "We're just waiting to turn the key," he said.
Obama's Crackdown on Whistleblowers
The NSA Four reveal how a toxic mix of cronyism and fraud blinded the agency before 9/11.
Tim Shorrock March 26, 2013 | This article appeared in the April 15, 2013 edition of The Nation
www.thenation.com/article/173521/obamas-crackdown-whistleblowers
"If this were a dictatorship, it would be a heck
of a lot easier, just so long as I'm the dictator."
-- George W. Bush, December 18, 2000
"A dictatorship would be a heck of a lot easier, there's no question
about it."
-- George W. Bush, July 26, 2001
JULIAN ASSANGE: A lot of people in the civil liberties community in the United States, in the privacy community in the rest of the world, and specialists, national security journalists like myself, had been following what the National Security Agency has been doing for a long time. We have been trying very hard to erect a debate. And there, yes, there were small debates, that really didn’t proceed anywhere. The lawsuits filed by the EFF and ACLU to try and get somewhere went nowhere, because they didn’t have the evidence. And what Edward Snowden revealed was documentary evidence, and it was that primary source evidence that has led to this debate. Everyone knows the difference—most people can’t even remember hearing about the National Security Agency prior to last year. Now everyone knows about it. And that is almost entirely as a result of these disclosures.
-- WikiLeaks’ Julian Assange Responds to Hillary Clinton: Fair U.S. Trial for Snowden "Not Possible"
WEDNESDAY, JULY 9, 2014
www.democracynow.org/2014/7/9/wikileaks_julian_assange_responds_to_hillary
http://space4peace.blogspot.com/2006/02/lying-and-spying-for-military-machine.html
Thursday, February 02, 2006
LYING AND SPYING FOR THE MILITARY MACHINE by Bruce Gagnon
My experience reveals that this problem of seeing the citizens as an enemy goes beyond Bush. The military industrial complex, the folks who really run our government, have for many years seen fit to label anyone who speaks out against their plan for global domination as a domestic enemy. Until we deal with the fact that we have lost our democracy to these big corporations, nothing much will change.
How to explain spying to a five year old:
December 28, 2005 - The New York Times
Defense Lawyers in Terror Cases Plan Challenges Over Spy Efforts
By ERIC LICHTBLAU
and JAMES RISEN
Trent Duffy, a spokesman for the White House, declined to comment in Crawford, Tex., when asked about a report in The New York Times that the security agency had tapped into some of the country's main telephone arteries to conduct broader data-mining operations in the search for terrorists.
But Mr. Duffy said: "This is a limited program. This is not about monitoring phone calls designed to arrange Little League practice or what to bring to a potluck dinner. These are designed to monitor calls from very bad people to very bad people who have a history of blowing up commuter trains, weddings and churches."
He added: "The president believes that he has the authority - and he does - under the Constitution to do this limited program. The Congress has been briefed. It is fully in line with the Constitution and also protecting American civil liberties."
NSA whistleblower Russ Tice on Boiling Frogs Podcast
June 19, 2013
NSA whistleblower Russel Tice told Peter B. Collins on Boiling Frog Post News (the website of high-level FBI whistleblower Sibel Edmonds):
[excerpt]
Tice: Okay. They went after–and I know this because I had my hands literally on the paperwork for these sort of things–they went after high-ranking military officers; they went after members of Congress, both Senate and the House, especially on the intelligence committees and on the armed services committees and some of the–and judicial. But they went after other ones, too. They went after lawyers and law firms. All kinds of–heaps of lawyers and law firms. They went after judges. One of the judges is now sitting on the Supreme Court that I had his wiretap information in my hand. Two are former FISA court judges. They went after State Department officials. They went after people in the executive service that were part of the White House–their own people. They went after antiwar groups. They went after U.S. international–U.S. companies that that do international business, you know, business around the world. They went after U.S. banking firms and financial firms that do international business. They went after NGOs that–like the Red Cross, people like that that go overseas and do humanitarian work. They went after a few antiwar civil rights groups. So, you know, don't tell me that there's no abuse, because I've had this stuff in my hand and looked at it. And in some cases, I literally was involved in the technology that was going after this stuff. And you know, when I said to [former MSNBC show host Keith] Olbermann, I said, my particular thing is high tech and you know, what's going on is the other thing, which is the dragnet. The dragnet is what Mark Klein is talking about, the terrestrial dragnet. Well my specialty is outer space. I deal with satellites, and everything that goes in and out of space. I did my spying via space. So that's how I found out about this.
Collins: Now Russ, the targeting of the people that you just mentioned, top military leaders, members of Congress, intelligence community leaders and the–oh, I'm sorry, it was intelligence committees, let me correct that–not intelligence community, and then executive branch appointees. This creates the basis, and the potential for massive blackmail.
Tice: Absolutely! And remember we talked about that before, that I was worried that the intelligence community now has sway over what is going on. Now here's the big one. I haven't given you any names. This was is summer of 2004. One of the papers that I held in my hand was to wiretap a bunch of numbers associated with, with a 40-something-year-old wannabe senator from Illinois. You wouldn't happen to know where that guy lives right now, would you? It's a big white house in Washington, DC. That's who they went after. And that's the president of the United States now.
www.newyorker.com/online/blogs/books/2013/06/the-nsas-chief-chronicler.html
 JUNE 10, 2013
JUNE 10, 2013
THE N.S.A.'S CHIEF CHRONICLER
POSTED BY ALEXANDER NAZARYAN
In 1982, long before most Americans ever had to think about warrantless eavesdropping, the journalist James Bamford published "The Puzzle Palace: A Report on N.S.A., America's Most Secret Agency," the first book to be written about the National Security Agency, which was started in 1952 by President Harry Truman to collect intelligence on foreign entities, and which we learned last week has been collecting the phone and Internet records of Americans and others. In the book, Bamford describes the agency as "free of legal restrictions" while wielding "technological capabilities for eavesdropping beyond imagination." He concludes with an ominous warning: "Like an ever-widening sinkhole, N.S.A.'s surveillance technology will continue to expand, quietly pulling in more and more communications and gradually eliminating more and more privacy." Three decades later, this pronouncement feels uncomfortably prescient: we were warned.
http://cryptome.org/nsa-bamford.htm
Statement - James Bamford, NSA Lawsuit Client
(Bamford joined an ACLU lawsuit against the NSA's warrantless wiretapping, but NSA is essentially beyond judicial review and the lawsuit was unsuccessful.)
James Bamford's book The Puzzle Palace was the first in-depth report on the US's largest spy agency. It is required reading for anyone who wants to know what the US government is. Here's a short review, followed by links to some chapters on-line:
www.namebase.org/sources/BY.html
Bamford, James. The Puzzle Palace: A Report on America's Most Secret Agency. Boston: Houghton Mifflin, 1982. 465 pages.
The National Security Agency is many times larger than the CIA, and since 1952 has spent many billions more per year. That didn't stop journalists from ignoring it, which suited NSA just fine. The story was too tough (or too career-threatening) for them; it took a mild-mannered, unassuming 35-year-old lawyer from Natick, Massachusetts to come along and blow the lid off. His only tools were persistence, shoe leather, and a tolerance for dusty library shelves in obscure archives. It was enough to get folks upset. The government reclassified some documents and warned Bamford "not to publish or communicate the information." Newsweek -- while grudgingly admitting that the book is "fascinating" and "revealing" -- spent more space quoting inside sources regarding the book's errors and insisted that "the threat the NSA poses to the privacy of Americans is not nearly so dire as Bamford would have it" (1982-09-06).
NSA is located in Fort Meade, Maryland in twenty buildings with a dozen acres of underground computers. In 1978 it controlled 68,000 people to listen in on the world's communications, analyze satellite eavesdropping systems, and develop and break codes. Numerous listening posts are spread around the globe, and 40 tons of classified documents are sent to the shredder each day. Your tax dollars are hard at work.
ISBN 0-395-31286-8
http://jya.com/pp08.htm
Source: The Puzzle Palace: A Report on America's Most Secret Agency, James Bamford,
Penguin Books, 1983. ISBN 0 14 00.6748 5. Pages 391-425.
Thanks to James Bamford and Penguin Books
Chapter 8 Partners
Chapter 9 Competition - On NSA's efforts to control public cryptography.
Chapter 10 Abyss - On NSA's expanding operations and attempts at legal controls.
The Agency That Could Be Big Brother
By JAMES BAMFORD
www.nytimes.com/2005/12/25/weekinreview/25bamford.html?pagewanted=2
Published: December 25, 2005
DEEP in a remote, fog-layered hollow near Sugar Grove, W.Va., hidden by fortress-like mountains, sits the country's largest eavesdropping bug. Located in a "radio quiet" zone, the station's large parabolic dishes secretly and silently sweep in millions of private telephone calls and e-mail messages an hour.
Run by the ultrasecret National Security Agency, the listening post intercepts all international communications entering the eastern United States. Another N.S.A. listening post, in Yakima,Wash., eavesdrops on the western half of the country.
A hundred miles or so north of Sugar Grove, in Washington, the N.S.A. has suddenly taken center stage in a political firestorm. The controversy over whether the president broke the law when he secretly ordered the N.S.A. to bypass a special court and conduct warrantless eavesdropping on American citizens has even provoked some Democrats to call for his impeachment.
According to John E. McLaughlin, who as the deputy director of the Central Intelligence Agency in the fall of 2001 was among the first briefed on the program, this eavesdropping was the most secret operation in the entire intelligence network, complete with its own code word - which itself is secret.
Jokingly referred to as "No Such Agency," the N.S.A. was created in absolute secrecy in 1952 by President Harry S. Truman. Today, it is the largest intelligence agency. It is also the most important, providing far more insight on foreign countries than the C.I.A. and other spy organizations.
But the agency is still struggling to adjust to the war on terror, in which its job is not to monitor states, but individuals or small cells hidden all over the world. To accomplish this, the N.S.A. has developed ever more sophisticated technology that mines vast amounts of data. But this technology may be of limited use abroad. And at home, it increases pressure on the agency to bypass civil liberties and skirt formal legal channels of criminal investigation. Originally created to spy on foreign adversaries, the N.S.A. was never supposed to be turned inward. Thirty years ago, Senator Frank Church, the Idaho Democrat who was then chairman of the select committee on intelligence, investigated the agency and came away stunned.
"That capability at any time could be turned around on the American people," he said in 1975, "and no American would have any privacy left, such is the capability to monitor everything: telephone conversations, telegrams, it doesn't matter. There would be no place to hide."
He added that if a dictator ever took over, the N.S.A. "could enable it to impose total tyranny, and there would be no way to fight back."
At the time, the agency had the ability to listen to only what people said over the telephone or wrote in an occasional telegram; they had no access to private letters. But today, with people expressing their innermost thoughts in e-mail messages, exposing their medical and financial records to the Internet, and chatting constantly on cellphones, the agency virtually has the ability to get inside a person's mind.
The N.S.A.'s original target had been the Communist bloc. The agency wrapped the Soviet Union and its satellite nations in an electronic cocoon. Anytime an aircraft, ship or military unit moved, the N.S.A. would know. And from 22,300 miles in orbit, satellites with super-thin, football-field-sized antennas eavesdropped on Soviet communications and weapons signals.
Today, instead of eavesdropping on an enormous country that was always chattering and never moved, the N.S.A. is trying to find small numbers of individuals who operate in closed cells, seldom communicate electronically (and when they do, use untraceable calling cards or disposable cellphones) and are constantly traveling from country to country.
During the cold war, the agency could depend on a constant flow of American-born Russian linguists from the many universities around the country with Soviet studies programs. Now the government is forced to search ethnic communities to find people who can speak Dari, Urdu or Lingala - and also pass a security clearance that frowns on people with relatives in their, or their parents', former countries.
According to an interview last year with Gen. Michael V. Hayden, then the N.S.A.'s director, intercepting calls during the war on terrorism has become a much more complex endeavor. On Sept. 10, 2001, for example, the N.S.A. intercepted two messages. The first warned, "The match begins tomorrow," and the second said, "Tomorrow is zero hour." But even though they came from suspected Al Qaeda locations in Afghanistan, the messages were never translated until after the attack on Sept. 11, and not distributed until Sept. 12.
What made the intercepts particularly difficult, General Hayden said, was that they were not "targeted" but intercepted randomly from Afghan pay phones.
This makes identification of the caller extremely difficult and slow. "Know how many international calls are made out of Afghanistan on a given day? Thousands," General Hayden said.
Still, the N.S.A. doesn't have to go to the courts to use its electronic monitoring to snare Al Qaeda members in Afghanistan. For the agency to snoop domestically on American citizens suspected of having terrorist ties, it first must to go to the Foreign Intelligence Surveillance Court, or FISA, make a showing of probable cause that the target is linked to a terrorist group, and obtain a warrant.
The court rarely turns the government down. Since it was established in 1978, the court has granted about 19,000 warrants; it has only rejected five. And even in those cases the government has the right to appeal to the Foreign Intelligence Surveillance Court of Review, which in 27 years has only heard one case. And should the appeals court also reject the warrant request, the government could then appeal immediately to a closed session of the Supreme Court.
Before the Sept. 11 attacks, the N.S.A. normally eavesdropped on a small number of American citizens or resident aliens, often a dozen or less, while the F.B.I., whose low-tech wiretapping was far less intrusive, requested most of the warrants from FISA.
Despite the low odds of having a request turned down, President Bush established a secret program in which the N.S.A. would bypass the FISA court and begin eavesdropping without warrant on Americans. This decision seems to have been based on a new concept of monitoring by the agency, a way, according to the administration, to effectively handle all the data and new information.
At the time, the buzzword in national security circles was data mining: digging deep into piles of information to come up with some pattern or clue to what might happen next. Rather than monitoring a dozen or so people for months at a time, as had been the practice, the decision was made to begin secretly eavesdropping on hundreds, perhaps thousands, of people for just a few days or a week at a time in order to determine who posed potential threats.
Those deemed innocent would quickly be eliminated from the watch list, while those thought suspicious would be submitted to the FISA court for a warrant.
In essence, N.S.A. seemed to be on a classic fishing expedition, precisely the type of abuse the FISA court was put in place to stop.At a news conference, President Bush himself seemed to acknowledge this new tactic. "FISA is for long-term monitoring," he said. "There's a difference between detecting so we can prevent, and monitoring."
This eavesdropping is not the Bush administration's only attempt to expand the boundaries of what is legally permissible.
In 2002, it was revealed that the Pentagon had launched Total Information Awareness, a data mining program led by John Poindexter, a retired rear admiral who had served as national security adviser under Ronald Reagan and helped devise the plan to sell arms to Iran and illegally divert the proceeds to rebels in Nicaragua.
Total Information Awareness, known as T.I.A., was intended to search through vast data bases, promising to "increase the information coverage by an order-of-magnitude." According to a 2002 article in The New York Times, the program "would permit intelligence analysts and law enforcement officials to mount a vast dragnet through electronic transaction data ranging from credit card information to veterinary records, in the United States and internationally, to hunt for terrorists." After press reports, the Pentagon shut it down, and Mr. Poindexter eventually left the government.
But according to a 2004 General Accounting Office report, the Bush administration and the Pentagon continued to rely heavily on data-mining techniques. "Our survey of 128 federal departments and agencies on their use of data mining," the report said, "shows that 52 agencies are using or are planning to use data mining. These departments and agencies reported 199 data-mining efforts, of which 68 are planned and 131 are operational." Of these uses, the report continued, "the Department of Defense reported the largest number of efforts."
The administration says it needs this technology to effectively combat terrorism. But the effect on privacy has worried a number of politicians.
After he was briefed on President Bush's secret operation in 2003, Senator Jay Rockefeller, the Democratic vice chairman of the Senate Select Committee on Intelligence, sent a letter to Vice President Dick Cheney.
"As I reflected on the meeting today and the future we face," he wrote, "John Poindexter's T.I.A. project sprung to mind, exacerbating my concern regarding the direction the administration is moving with regard to security, technology, and surveillance."
Senator Rockefeller sounds a lot like Senator Frank Church.
"I don't want to see this country ever go across the bridge," Senator Church said. "I know the capacity that is there to make tyranny total in America, and we must see to it that this agency and all agencies that possess this technology operate within the law and under proper supervision, so that we never cross over that abyss. That is the abyss from which there is no return."James Bamford is the author of "Puzzle Palace" and "Body of Secrets: Anatomy of the Ultra-Secret National Security Agency."
www.bloomberg.com/news/2013-06-23/u-s-surveillance-is-not-aimed-at-terrorists.html
U.S. Surveillance Is Not Aimed at Terrorists
By Leonid Bershidsky Jun 23, 2013 3:00 PM PT
The debate over the U.S. government's monitoring of digital communications suggests that Americans are willing to allow it as long as it is genuinely targeted at terrorists. What they fail to realize is that the surveillance systems are best suited for gathering information on law-abiding citizens.
People concerned with online privacy tend to calm down when told that the government can record their calls or read their e-mail only under special circumstances and with proper court orders. The assumption is that they have nothing to worry about unless they are terrorists or correspond with the wrong people.
The infrastructure set up by the National Security Agency, however, may only be good for gathering information on the stupidest, lowest-ranking of terrorists. The Prism surveillance program focuses on access to the servers of America's largest Internet companies, which support such popular services as Skype, Gmail and iCloud. These are not the services that truly dangerous elements typically use.
NSA spying flap extends to contents of U.S. phone calls
Declan McCullagh, June 15, 2013
excerpt:
Earlier reports have indicated that the NSA has the ability to record nearly all domestic and international phone calls -- in case an analyst needed to access the recordings in the future. A Wired magazine article last year disclosed that the NSA has established "listening posts" that allow the agency to collect and sift through billions of phone calls through a massive new data center in Utah, "whether they originate within the country or overseas." That includes not just metadata, but also the contents of the communications.
William Binney, a former NSA technical director who helped to modernize the agency's worldwide eavesdropping network, told the Daily Caller this week that the NSA records the phone calls of 500,000 to 1 million people who are on its so-called target list, and perhaps even more. "They look through these phone numbers and they target those and that's what they record," Binney said.
Brewster Kahle, a computer engineer who founded the Internet Archive, has vast experience storing large amounts of data. He created a spreadsheet this week estimating that the cost to store all domestic phone calls a year in cloud storage for data-mining purposes would be about $27 million per year, not counting the cost of extra security for a top-secret program and security clearances for the people involved.
NSA's annual budget is classified but is estimated to be around $10 billion.
Documents that came to light in an EFF lawsuit provide some insight into how the spy agency vacuums up data from telecommunications companies. Mark Klein, who worked as an AT&T technician for over 22 years, disclosed in 2006 (PDF) that he witnessed domestic voice and Internet traffic being surreptitiously "diverted" through a "splitter cabinet" to secure room 641A in one of the company's San Francisco facilities. The room was accessible only to NSA-cleared technicians.
www.truthout.org/docs_2005/122505F.shtml
Some Fear Eavesdropping Could Undermine Work of Spy Agency
By Warren P. Strobel and Jonathan S. Landay
Knight Ridder Newspapers
Friday 23 December 2005
Web snooping vital, spy agency boss says
Oct. 22, 2005. 10:27 AM
MICHELLE SHEPHARD
STAFF REPORTER
Toronto
Star
OTTAWA—The head of Canada's eavesdropping agency says it needs to own
the Internet to combat terrorism.
www.danbrown.com/novels/digital_fortress/interview.html
DIGITAL FORTRESS, the controversial thriller about the ultra-secret U.S. National Security Agency, spent 15 weeks as the #1 national bestselling E-book and was inspired by a true event.
AUTHOR INTERVIEW
"I couldn't figure out how the Secret Service knew what these kids were saying in their E-mail."Q: A rather startling event inspired you to write Digital Fortress. Can you elaborate on what happened?
A: A few years ago, I was teaching on the campus of Phillips Exeter Academy in New Hampshire. One Spring day, unannounced, the U.S. Secret Service showed up and detained one of our students claiming he was a threat to national security. As it turned out, the kid had sent private E-mail to a friend saying how much he hated President Clinton and how he thought the president should be shot. The Secret Service came to campus to make sure the kid wasn't serious. After some interrogation the agents decided the student was harmless, and not much came of it. Nonetheless, the incident really stuck with me. I couldn't figure out how the secret service knew what these kids were saying in their E-mail.
I began doing some research into where organizations like the Secret Service get their intelligence data, and what I found out absolutely floored me. I discovered there is an intelligence agency as large as the CIA... that only about 3% of Americans knows exists.
It is called the National Security Agency (NSA), and it is home to the country's eavesdroppers. The agency functions like an enormous vacuum cleaner sucking in intelligence data from around the globe and processing it for subversive material. The NSA's super-computers scan E-mail and other digital communiqués looking for dangerous word combinations like "kill" and "Clinton" in the same sentence.
The more I learned about this ultra-secret agency and the fascinating moral issues surrounding national security and civilian privacy, the more I realized it was a great backdrop for a novel. That's when I started writing Digital Fortress.
"The NSA is in charge of waging the information war-- stealing other people's secrets while protecting our own." ....Q: Does the government really read our E-mail?
A: Government monitoring of civilian communication is something that has been going on for decades. Even though the public is widely unaware, government officials and specialists in privacy-related fields are certainly aware of the practice. The debate over its ethics is complex because a precedent exists that intercepting certain E-mail, cellular phone, and FAX communications can help law-enforcement officials catch dangerous criminals. The question turns into one of civilian privacy vs. national security. In the 1950's the NSA's then top-secret Project Shamrock intercepted and scanned all telegrams sent in or out of the country; ITT and Western Union were under enormous political pressure to cooperate silently...and they did so.
Project Shamrock stayed in effect until 1975. Nixon's Huston Plan and later Project Minaret further relaxed regulations on monitoring civilian communications and even activated enormous watch-lists of U.S. civilians whose communiqués were regularly tapped. Just recently, of course, the FBI caught the infamous hacker Jose Ardita by secretly monitoring computer activity at Harvard University. As you can see, this sort of activity is nothing new.
NSA JUST ONE OF MANY AGENCIES SPYING ON AMERICANS
www.capitolhillblue.com/artman/publish/article_7904.shtml
DOUG THOMPSON, CAPITOL HILL BLUE - Spying on Americans by the super-secret National Security Agency is not only more widespread than President George W. Bush admits but is part of a concentrated, government-wide effort to gather and catalog information on U.S. citizens, sources close to the administration say. Besides the NSA, the Pentagon, Federal Bureau of Investigation, the Department of Homeland Security and dozens of private contractors are spying on millions of Americans 24 hours a day, seven days a week, 365 days a year. "It's a total effort to build dossiers on as many Americans as possible," says a former NSA agent who quit in disgust over use of the agency to spy on Americans. "We're no longer in the business of tracking our enemies. We're spying on everyday Americans."
"It's really obvious to me that it's a look-at-everything type program," says cryptology expert Bruce Schneier. Schneier says he suspects that the NSA is turning its massive spy satellites inward on the United States and intentionally gathering vast streams of raw data from many more people than disclosed to date - potentially including all e-mails and phone calls within the United States. But the NSA spying is just the tip of the iceberg.
Although supposedly killed by Congress more than 18 months ago, the Defense Advance Project Research Agency's Terrorist Information Awareness system, formerly called the "Total Information Awareness" program, is alive and well and collecting data in real time on Americans at a computer center located at 3801 Fairfax Drive in Arlington, Virginia. . . "TIA builds a profile of every American who travels, has a bank account, uses credit cards and has a credit record," says security expert Allen Banks. "The profile establishes norms based on the person's spending and travel habits. Then the system looks for patterns that break from the norms, such of purchases of materials that are considered likely for terrorist activity, travel to specific areas or a change in spending habits.". . .
In her book Army Surveillance in America, historian Joan M. Jensen noted, "What began as a system to protect the government from enemy agents became a vast surveillance system to watch civilians who violated no law but who objected to wartime policies or to the war itself." "It's a fucking nightmare," says a congressional aide who recently obtained information on the program for his boss but asked not to be identified because he fears retaliation from the Bush administration. "We're collecting more information on Americans than on real enemies of our country."
www.truthout.org/docs_2005/122605I.shtml
Big Brother Bush Is Listening
By Marjorie Cohn
t r u t h o u t | Perspective
Monday 26 December 2005
www.truthout.org/docs_2005/122705B.shtml
The Hidden State Steps Forward
By Jonathan Schell
The Nation
09 January 2006 Edition
The alarming argument is that as Commander in Chief he possesses "inherent" authority to suspend laws in wartime. But if he can suspend FISA at his whim and in secret, then what law can he not suspend? What need is there, for example, to pass or not pass the Patriot Act if any or all of its provisions can be secretly exceeded by the President? ....
If Congress accepts his usurpation of its legislative power, they will be no Congress and might as well stop meeting. Either the President must uphold the laws of the United States, which are Congress's laws, or he must leave office.
LETTERS TO THE EDITOR
At the sound of the beep . . . Posted December 31, 2005 - Orlando Sentinel
I've included a sample script below that may be helpful to your readers when recording an outgoing message on their answering machine in the future in light of President Bush's determination to continue to use the NSA to spy on American citizens:
Hello, you've reached 407- -------- . I'm sorry I'm not available to take your call at this time.
It's really not necessary to leave your name, number, time you called, where you called from, date of birth, place of employment, mother's maiden name, Social Security number or shoe size; the government already has that information.
Please just leave a brief message after the beep and the National Security Agency will record the call and get back to you at its earliest possible convenience.
BEEP. . . .
Doug De Clue
Orlando
http://arstechnica.com/news.ars/post/20051220-5808.html
The new technology at the root of the NSA wiretap scandal
12/20/2005
.... The domestic electronic surveillance ball really got rolling under the Clinton administration, with the 1994 Communications Assistance for Law Enforcement Act (CALEA). CALEA mandated that the telcos aid wiretapping by installing remote wiretap ports onto their digital switches so that the switch traffic would be available for snooping by law enforcement. After CALEA passed, the FBI no longer had to go on-site with wiretapping equipment in order to tap a line--they could monitor and digitally process voice communications from the comfort of the home office. (The FCC has recently ruled that CALEA covers VOIP services, which means that providers like Vonage will have to find a way to comply.)
CALEA opened up a huge can of worms, and PGP creator Phil Zimmermann sounded the alarm back in 1999 about where the program was headed:
A year after the CALEA passed, the FBI disclosed plans to require the phone companies to build into their infrastructure the capacity to simultaneously wiretap 1 percent of all phone calls in all major U.S. cities. This would represent more than a thousandfold increase over previous levels in the number of phones that could be wiretapped. In previous years, there were only about a thousand court-ordered wiretaps in the United States per year, at the federal, state, and local levels combined. It's hard to see how the government could even employ enough judges to sign enough wiretap orders to wiretap 1 percent of all our phone calls, much less hire enough federal agents to sit and listen to all that traffic in real time. The only plausible way of processing that amount of traffic is a massive Orwellian application of automated voice recognition technology to sift through it all, searching for interesting keywords or searching for a particular speaker's voice. If the government doesn't find the target in the first 1 percent sample, the wiretaps can be shifted over to a different 1 percent until the target is found, or until everyone's phone line has been checked for subversive traffic. The FBI said they need this capacity to plan for the future. This plan sparked such outrage that it was defeated in Congress. But the mere fact that the FBI even asked for these broad powers is revealing of their agenda.
Read the quote above carefully, and see if it doesn't ring any bells for you. The salient points that Zimmermann makes are these:
- In 1995, back when the Pentium Pro was hot stuff, the FBI requested the legal authorization to do very high-volume monitoring of digital calls.
- There's no way for the judicial system to approve warrants for the number of calls that the FBI wanted to monitor.
- The agency could never hire enough humans to be able to monitor that many calls simultaneously, which means that they'd have to use voice recognition technology to look for "hits" that they could then follow up on with human wiretaps.
It is entirely possible that the NSA technology at issue here is some kind of high-volume, automated voice recognition and pattern matching system. Now, I don't at all believe that all international calls are or could be monitored with such a system, or anything like that. Rather, the NSA could very easily narrow down the amount of phone traffic that they'd have to a relatively small fraction of international calls with some smart filtering. First, they'd only monitor calls where one end of the connection is in a country of interest. Then, they'd only need the ability to do a roving random sample of a few seconds from each call in that already greatly narrowed pool of calls. As Zimmermann describes above, you monitor a few seconds of some fraction of the calls looking for "hits," and then you move on to another fraction. If a particular call generates a hit, then you zero in on it for further real-time analysis and possible human interception. All the calls can be recorded, cached, and further examined later for items that may have been overlooked in the real-time analysis. [emphases added]
http://arstechnica.com/news.ars/post/20051220-5813.html
NSA wiretap followup: Why computer-automated mass surveillance is a bad idea
12/20/2005
In the end, brute force security techniques are not only corrosive to democratic values but they're also bad for national security. They waste massive resources that could be spent more effectively elsewhere, and they give governments and countries a false sense of security that a savvy enemy can exploit to devastating effect.
I'll wrap this post up with a story that shows just how old, and just how ineffective, brute force "search and seizure" tactics are, even when the field has been narrowed using intelligently selected criteria.
A Greek religious text from antiquity tells of a king who got word that a potential usurper to his throne had been born somewhere in his kingdom. He wanted to find this baby and kill it, but the unwitting human assets that he was using to lead him to the child's location got wind of his intentions and managed to slip away. So all the king knew was the sex of the child (male), the city where the child was born, and a rough estimate of the child's birth date. Targeted human intelligence having failed him, he decided to try the brute force approach. He had all the male children in that city that were two years of age or under killed.
After the slaughter of all of those infants, the king sat back in relief. The child could never have escaped that massacre! His kingdom was safe. But unbeknownst to the king, his plan hadn't worked. In spite of the fact that the king had narrowed his search using perfectly sound criteria, the boy and his parents still managed to escape to Egypt, and all of those other children died for nothing. And to top it all off, the boy Jesus wasn't even a real threat to Herod's throne. It was a false alarm! Herod, in his paranoia, had misinterpreted the original intelligence data as pointing to a threat, but in reality it signified no such thing... which brings me to my final point: it's not just enough to have sound intelligence; you also need political leaders who have the wisdom to use that intelligence appropriately.
Powers of 1,000 (or 1,024, if you want to be precisely accurate).
Megabyte is roughly a million bytes. (10 to the 6th power)
Gigabyte is roughly a billion (US) bytes. (10 to the 9th)
Terabyte is roughly a trillion bytes. (10 to the 12th)
Petabyte is roughly a quadrillion bytes. (10 to the 15th)
Exabyte is roughly
a quintillion bytes. (10 to the 18th)
Zettabyte is roughly
a sixtillion bytes. (10 to the 21st)
Yottabyte is roughly a septillion bytes. (10 to the 24th).
Yottabyte databases are the scale of what the National Security Agency is reportedly implementing with its new facilities at Fort Gordon, Georgia, San Antonio, Texas and Bluffdale, Utah. Each of these new data centers are on separate power grids - the eastern US, the western US and Texas have separate electrical systems. Is this a coincidence or is the NSA planning for redundancy if there are major crashes to the US electric power system?
The NSA Is Building the Country's Biggest Spy Center
www.wired.com/threatlevel/2012/03/ff_nsadatacenter/all/
Mar 15, 2012 – But the agency rejected the idea, and, given the massive new storage facility in Utah, Binney suspects that it now simply collects everything.
www.democracynow.org/2012/4/20/exclusive_national_security_agency_whistleblower_william
FRIDAY, APRIL 20, 2012
Exclusive: National Security Agency Whistleblower William Binney on Growing State Surveillance
In his first television interview since he resigned from the National Security Agency over its domestic surveillance program, William Binney discusses the NSA's massive power to spy on Americans and why the FBI raided his home after he became a whistleblower. Binney was a key source for investigative journalist James Bamford's recent exposé in Wired Magazine about how the NSA is quietly building the largest spy center in the country in Bluffdale, Utah. The Utah spy center will contain near-bottomless databases to store all forms of communication collected by the agency, including private emails, cellphone calls, Google searches and other personal data.
Binney served in the NSA for over 30 years, including a time as technical director of the NSA's World Geopolitical and Military Analysis Reporting Group. Since retiring from the NSA in 2001, he has warned that the NSA's data-mining program has become so vast that it could "create an Orwellian state." Today marks the first time Binney has spoken on national television about NSA surveillance.
www.nytimes.com/2012/08/23/opinion/the-national-security-agencys-domestic-spying-program.html?_r=0
The Program: The filmmaker Laura Poitras profiles William Binney, a 32-year veteran of the National Security Agency who helped design a top-secret program he says is broadly collecting Americans' personal data.
By LAURA POITRAS
Published: August 22, 2012
It took me a few days to work up the nerve to phone William Binney. As someone already a "target" of the United States government, I found it difficult not to worry about the chain of unintended consequences I might unleash by calling Mr. Binney, a 32-year veteran of the National Security Agency turned whistle-blower. He picked up. I nervously explained I was a documentary filmmaker and wanted to speak to him. To my surprise he replied: "I'm tired of my government harassing me and violating the Constitution. Yes, I'll talk to you."
Two weeks later, driving past the headquarters of the N.S.A. in Maryland, outside Washington, Mr. Binney described details about Stellar Wind, the N.S.A.'s top-secret domestic spying program begun after 9/11, which was so controversial that it nearly caused top Justice Department officials to resign in protest, in 2004.
"The decision must have been made in September 2001," Mr. Binney told me and the cinematographer Kirsten Johnson. "That's when the equipment started coming in." In this Op-Doc, Mr. Binney explains how the program he created for foreign intelligence gathering was turned inward on this country. He resigned over this in 2001 and began speaking out publicly in the last year. He is among a group of N.S.A. whistle-blowers, including Thomas A. Drake, who have each risked everything — their freedom, livelihoods and personal relationships — to warn Americans about the dangers of N.S.A. domestic spying.
www.zeit.de/datenschutz/malte-spitz-data-retention
track a German politician's movements, courtesy of data retention by the telephone company
www.networkworld.com/news/2011/121511-government-surveillance-254137.html
The storage needed for different types of data varies widely. Data to pinpoint a location within 15 feet takes up 75 bits. Storing that data for 1 million people taken at five-minute intervals for a year would take up less than a terabyte and cost a bit more than $50.
In 2015 the cost of storing all the phone calls made in a year by an average person will be less than 2 cents, the report says. By 2020, the cost to store all the phone calls made by everyone over the age of 14 in Iran will be about $100,000, the report says.
Villaseno points to a 24-hour video surveillance program in China that will put 500,000 video cameras throughout the city of Chongquing. By 2020, all that video could be stored for 25 cents per Chongquing resident per year.
Recording Everything/ Digital Storage as an Enabler of Authoritarian Governments - Brookings Institution
www.brookings.edu/papers/2011/1214_digital_storage_villasenor.aspx
www.theatlanticwire.com/national/2012/08/nypd-microsoft-hope-make-mint-new-surveillance-system/55561/
retroactive surveillance is here (keeping track of ALL electronic communications, license plate trackers, electronic tags for public transit - allows for a "rewind" through someone's activities should they become of interest to the permanent state).
The real issue with the domestic -- and global -- spying by the NSA is not what they are doing, but why are they so concerned about watching everything that everyone does? It's not about listening to everyone in real time, but recording as much as can be gobbled up in case anyone becomes "a person of interest" and then their entire electronic communication archive can be retrieved along with the network of who someone communicates with. This particularly applies to journalists, politicians, business leaders and other elites.
Pentagon think tanks have long looked at the limits to endless growth, even if they don't discuss these topics with the rank and file soliders and sailors, nor the mere citizens who are taxed to pay for Empire. The military has known for a long time about Peak Energy -- controlling the world's oil fields and supply routes is a primary motivation for their quest for global military domination, including the invasion of Iraq. In addition, they are expecting Climate Change to destabilize the world through increased refugee flows, economic collapse, food shortages and other consequences. These tragedies are going to stress every society, including the United States. The domestic "warrantless wiretapping" is not really an effort to prevent foreign terrorism. Instead, it is preparation for the economic, energy and ecological unraveling over the coming years and decades -- a population monitoring system to track dissent.
Details on official preparations for the descent:
www.oilempire.us/peak-fascism.html
Peak Fascism: Peaked Oil, Climate Chaos, Civil Liberties
An excellent analysis of the NSA monitoring as preparation for collapse:
www.guardian.co.uk/environment/earth-insight/2013/jun/14/climate-change-energy-shocks-nsa-prism
Pentagon bracing for public dissent over climate and energy shocks
NSA Prism is motivated in part by fears that environmentally-linked disasters could spur anti-government activism
"At 12:01 On the morning of November 4, 1952, a new federal agency was born.
Unlike other such bureaucratic births, however, this one arrived in silence.
No news coverage, no congressional debate, no press announcement, not even the
whisper of a rumor. Nor could any mention of the new organization be found in
the Government Organization Manual of the Federal Register or the Congressional
Record. Equally invisible were the new agency's director, its numerous buildings,
and its ten thousand employees.
"Eleven days earlier, on October 24, President Harry S Truman scratched his signature
on the bottom of a seven-page presidential memorandum addressed to secretary
of State Dean G. Acheson and Secretary of Defense Robert A. Lovett. Classified
top secret and stamped with a code word that was itself classified, the order
directed the establishment of an agency to be known as the National Security
Agency. It was the birth certificate for America's newest and most secret agency,
so secret in fact that only a handful in the government would be permitted to
know of its existence."
-- James Bamford, The Puzzle Palace (1982) at 15.
A 20707 5/4/54/OSO
NSA TS CONTL. NO 73-00405
COPY: D321
Oct 24 1952
MEMORANDUM FOR: The Secretary of State
The Secretary of Defense
SUBJECT: Communications Intelligence Activities
The communications intelligence (COMINT) activities of the United States are a national responsibility. They must be so organized and managed as to exploit to the maximum the available resources in all participating departments and agencies and to satisfy the legitimate intelligence requirements of all such departments and agencies.
I therefore designate the Secretaries of State and Defense as a Special Committee of the National Security Council for COMINT, which Committee shall, with the assistance of the Director of Central Intelligence, establish policies governing COMINT activities. and keep me advised of such policies through the Executive Secretary of the National Security Council.
I further designate the Department of Defense as executive agent of the Government, for the production of COMINT information.
I direct this Special Committee to prepare and issue directives which shall include the provisions set forth below and such other provisions as the Special Committee may determine to be necessary.
- A directive to the United States Communication Intelligence Board (USCIB). This directive will replace the National Security Council Intelligence Directive No. 9, and shall prescribe USCIB's new composition, responsibilities and procedures in the COMINT fields. This directive shall include the following provisions.
- USCIB shall be reconstituted as a body acting for and under the Special Committee, and shall operate in accordance with the provisions of the new directive. Only those departments or agencies represented in USCIB are authorized to engage in COMINT activities.
- The Board shall be composed of the following members:
- The Director of Central Intelligence, who shall be the Chairman of the Board.
- A representative of the Secretary of State.
- A representative of the Secretary of Defense
- A representative of the Director of the Federal Bureau of Investigation.
- The Director of the National Security Agency.
- A representative of the Department of the Army.
- A representative of the Department of the Navy.
- A representative of the Department of the Air Force.
- A representative of the Central Intelligence Agency.
- The Board shall have a staff headed by an executive secretary who shall be appointed by the Chairman with the approval of the majority of the Board.
- It shall be the duty of the Board to advise and make recommendations to the Secretary of Defense, in accordance with the following procedure, with respect to any matter relating to communications intelligence which falls within the jurisdiction of the Director of the NSA.
- The Board shall reach its decision by majority vote. Each member of the Board shall have one vote except the representatives of the Secretary of State and of the Central Intelligence Agency who shall each have two votes. The Director of Central Intelligence, as Chairman, will have no vote. In the event that the Board votes and reaches a decision, any dissenting member of the Board may appeal from such decision within 7 days of the Special Committee. In the event that the Board votes but fails to reach a decision, any member of the Board may appeal within 7 days to the Special Committee. In either event the Special Committee shall review the matter, and its determination thereon shall be final. Appeals by the Director of NSA and/or the representatives of the Military Departments shall only be filed with the approval of the Secretary of Defense.
- If any matter is voted on by the Board but -
- no decision is reached and any member files an appeal;
- a decision is reached in which the representative of the Secretary of Defense does not concur and files an appeal; no action shall be taken with respect to the subject matter until the appeal is decided, provided that, if the Secretary of Defense determines, after consultation with the Secretary of State, that the subject matter presents a problem of an emergency nature and requires immediate action, his decision shall govern, pending the result of the appeal. In such an emergency situation the appeal may be taken directly to the President.
- Recommendations of the Board adopted in accordance with the foregoing procedures shall be binding on the Secretary of Defense. Except on matter which have been voted on by the Board, the Director of NSA shall discharge his responsibilities in accordance with his own judgment, subject to the direction of the Secretary of Defense.
- The Director of NSA shall make such reports and furnish such information from time to time to the Board, either orally or in writing, as the Board may request, and shall bring to the attention of the Board either in such reports or otherwise any major policies or programs in advance of their adoption by him.
- It shall also be the duty of the Board as to matters not falling within the jurisdiction of NSA;
- To coordinate the communications intelligence activities among all departments and agencies authorized by the President to participate therein;
- To initiate, to formulate policies concerning, and subject to the provision of NSCID No. 5, to supervise all arrangements with foreign governments in the field of communications intelligence; and
- to consider and make recommendations concerning policies relating to communications intelligence of common interest to the departments and agencies, including security standards and practices, and, for this purpose, to investigate and study the standards and practices of such departments and agencies in utilizing and protecting COMINT information.
- Any recommendation of the Board with respect to the matters described in paragraph e above shall be binding on all departments or agencies of the Government if it is adopted by the unanimous vote of the members of the Board. Recommendations approved by the majority, but not all, of the members of the Board shall be transmitted by it to the Special Committee for such action as the Special Committee may see fit to take.
- The Board will meet monthly, or oftener at the call of the Chairman or any member, and shall determine its own procedures.
A directive to the Secretary of Defense. This directive shall include the following provisions:
- Subject to the specific provisions of this directive, the Secretary of Defense may delegate in whole of in part authority over the Director of NSA within his department as he sees fit.
- The COMINT mission of the National Security Agency (NSA) shall be to provide an effective, unified organization and control of the communications intelligence activities of the United States conducted against foreign governments, to provide for integrated operational policies and procedures pertaining thereto. As used in this directive, the terms "communications intelligence" or "COMINT" shall be construed to mean all procedures and methods used in the interception of communications other than foreign press and propaganda broadcasts and the obtaining of information from such communications by other than intended recipients, but shall exclude censorship and the production and dissemination of finished intelligence.
- NSA shall be administered by a Director, designated by the Secretary of Defense after consultation with the Joint Chiefs of Staff, who shall serve for a minimum term of 4 years and who shall be eligible for reappointment. The Director shall be a career commissioned officer of the armed services on active or reactivated status, and shall enjoy at least 3-star rank during the period of his incumbency.
- Under the Secretary of Defense, and in accordance with approved policies of USCIB, the Director of NSA shall be responsible for accomplishing the mission of NSA. For this purpose all COMINT collection and production resources of the United States are placed under his operational and technical control. When action by the Chiefs of the operating agencies of the Services or civilian departments or agencies is required, the Director shall normally issue instruction pertaining to COMINT operations through them. However, due to the unique technical character of COMINT operations, the Director is authorized to issue direct to any operating elements under his operational control task assignments and pertinent instructions which are within the capacity of such elements to accomplish. He shall also have direct access to, and direct communication with, any elements of the Service or civilian COMINT agencies on any other matters of operational and technical control as may be necessary, and he is authorized to obtain such information and intelligence material from them as he may require. All instruction issued by the Director under the authority provided in this paragraph shall be mandatory, subject only to appeal to the Secretary of Defense by the Chief of Service or head of civilian department of agency concerned.
- Specific responsibilities of the Director of NSA include the following:
- Formulating necessary operational plans and policies for the conduct of the U.S. COMINT activities.
- Conducting COMINT activities, including research and development, as required to meet the needs of the departments and agencies which are authorized to receive the products of COMINT.
- Determining, and submitting to appropriate authorities, requirements for logistic support for the conduct of COMINT activities, together with specific recommendations as to what each of the responsible departments and agencies of the Government should supply.
- Within NSA's field of authorized operations prescribing requisite security regulations covering operating practices, including the transmission, handling and distribution of COMINT material within and among the COMINT elements under his operations or technical control; and exercising the necessary monitoring and supervisory control, including inspections if necessary, to ensure compliance with the regulations.
- Subject to the authorities granted the Director Central Intelligence under NSCID No. 5, conducting all liaison on COMINT matters with foreign governmental communications intelligence agencies.
- To the extent he deems feasible and in consonance with the aims of maximum over-all efficiency, economy, and effectiveness, the Director shall centralize or consolidate the performance of COMINT functions for which he is responsible. It is recognized that in certain circumstances elements of the Armed Forces and other agencies being served will require close COMINT support. Where necessary for this close support, direct operational control of specified COMINT facilities and resources will be delegated by the Director, during such periods and for such tasks as are determined by him, to military commanders or to the Chiefs of other agencies supported.
- The Director shall exercise such administrative control over COMINT activities as he deems necessary to the effective performance of his mission. Otherwise, administrative control of personnel and facilities will remain with the departments and agencies providing them.
- The Director shall make provision for participation by representatives of each of the departments and agencies eligible to receive COMINT products in those offices of NSA where priorities of intercept and processing are finally planned.
- The Director shall have a civilian deputy whose primary responsibility shall be to ensure the mobilization and effective employment of the best available human and scientific resources in the field of cryptographic research and development.
- Nothing in this directive shall contravene the responsibilities of the individual departments and agencies for the final evaluation of COMINT information, its synthesis with information from other sources, and the dissemination of finished intelligence to users.
The special nature of COMINT actives requires that they be treated in all respects as being outside the framework of other or general intelligence activities. Order, directives, policies, or recommendations of any authority of the Executive Branch relating to the collection, production, security, handling, dissemination, or utilization of intelligence, and/or classified material, shall not be applicable to COMINT actives, unless specifically so stated and issued by competent departmental of agency authority represented on the Board. Other National Security Council Intelligence Directive to the Director of Central Intelligence and related implementing directives issued by the Director of Central Intelligence shall be construed as non-applicable to COMINT activities, unless the National Security Council has made its directive specifically applicable to COMINT.
/s/ HARRY S TRUMAN
European Parliament - Final Report on Echelon, 11 July 2001
www.cryptome.org/echelon-ep-fin.htm
MINORITY OPINION by Patricia McKenna and Ilka Schröder
This report makes an important point in emphasising that Echelon does exist, but it stops short of drawing political conclusions. It is hypocritical for the European Parliament to criticise the Echelon interception practice while taking part in plans to establish a European Secret Service.
No effective public control mechanism of secret services and their undemocratic practices exists globally. It is in the nature of secret services that they cannot be controlled. They must therefore be abolished. This report serves to legitimise a European Secret Service which will infringe fundamental rights - just as Echelon does.
For the majority in Parliament, the focus is industry, where profit interests are supposedly threatened by industrial espionage. However, the vital issue is that no one can communicate in confidence over distances any more. Political espionage is a much greater threat than economic espionage.
This report constantly plays down these dangers of Echelon, while it remains silent about plans to introduce the ENFOPOL interception system in the EU. Every society must take a fundamental decision whether or not to live under permanent control. By adopting this report, the European Parliament shows that it is not concerned about protecting human rights and citizens’ liberties.
www.fas.org/irp/program/process/echelon.htm
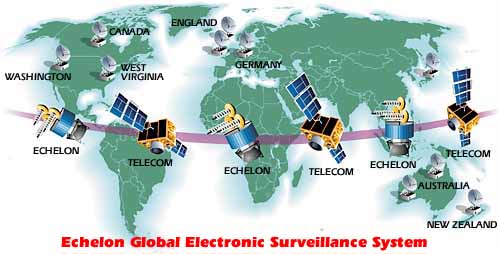
ECHELON is a term associated with a global network of computers that automatically search through millions of intercepted messages for pre-programmed keywords or fax, telex and e-mail addresses. Every word of every message in the frequencies and channels selected at a station is automatically searched. The processors in the network are known as the ECHELON Dictionaries. ECHELON connects all these computers and allows the individual stations to function as distributed elements an integrated system. An ECHELON station's Dictionary contains not only its parent agency's chosen keywords, but also lists for each of the other four agencies in the UKUSA system [NSA, GCHQ, DSD, GCSB and CSE]

Echelon is a partnership of five countries: US, Britain, Canada, Australia, New Zealand
New Navy-supported machine recognizes spoken words better than humans NAVY WIRE SERVICE (NWS) - November 1, 1999 -- In benchmark testing, USC's speech recognition system bested all existing computer systems and outperformed the keenest human ears.
Machine Demonstrates Superhuman Speech Recognition Abilities University of Southern California News Service Release date: 9/30/99 -- The system can distinguished words in vast amounts of random "white" noise — noise with amplitude 1,000 times the strength of the target auditory signal. Human listeners can deal with only a fraction as much. And the system can pluck words from the background clutter of other voices — the hubbub heard in bus stations, theater lobbies and cocktail parties, for example. With just a minor adjustment, the system can identify different speakers of the same word with superhuman acuity.
www.fas.org/irp/nsa/
NATIONAL SECURITY AGENCY
Resources from the Federation of American Scientists
www.fas.org/irp/nsa/ncs21/index.html
National Cryptologic Strategy for the 21st Century
These pages outline the National Security Agency/Central Security Service's strategic plan for the 21st century, and how we intend to achieve our goal: information superiority for America.
www.fas.org/irp/nic/index.html
National Intelligence Council
http://duncan.gn.apc.org/echelon-dc.htm
NEW STATESMAN
12 August 1988
Cover, pages 10-12
Somebody's listening
http://prorev.com/2005/12/liberals-in-denial.htm
Echelon didn't have to target people since it was based in part on intercepting messages and selected those with key words in them like "bomb." Further, the reason Echelon didn't - and didn't have to - comply with FISA was subtly revealed by Tenet in his testimony: "We do not target their conversations for collection in the United States. . ." Right, and that's because Echelon did much of its work outside the United States. And that's why its stations weren't in the U.S. just as today, many U.S. concentration camps are not in this country.
Some day, liberals are going to have to accept the fact that this country has moved further to the right under every president beginning with Reagan and including Clinton.
www.fas.org/irp/eprint/sp/sp_c2.htm
Secret Power: New Zealand's Role in the International Spy Network
by Nicky Hager
Chapter Two:
Hooked up to the spy network:
The UKUSA system
The U.S. Intelligence Community
Jeffrey T. Richelson
New York, Ballinger, 1989
This excerpt from Second Edition (soft), pp. 167-197167
Chapter 8
SIGNALS INTELLIGENCE
http://jya.com/usic12.htm
Chapter 12
EXCHANGE AND LIAISON
ARRANGEMENTS
29 April 1998
Thanks to William Burrows and Berkley Books
Deep Black:
Space Espionage and National Security
William Burrows
New York, Random House, 1986
This excerpt from Berkley Books (soft), 1988, pp. 167-191, 358-361Chapter 8
FOREIGN BASES:
A NET SPREAD WIDE
www.mcclatchydc.com/2013/06/26/195045/memories-of-stasi-color-germans.html
 Memories of Stasi color Germans' view of U.S. surveillance programs
Memories of Stasi color Germans' view of U.S. surveillance programs
By Matthew Schofield | McClatchy Washington Bureau
BERLIN — Wolfgang Schmidt was seated in Berlin's 1,200-foot-high TV tower, one of the few remaining landmarks left from the former East Germany. Peering out over the city that lived in fear when the communist party ruled it, he pondered the magnitude of domestic spying in the United States under the Obama administration. A smile spread across his face.
"You know, for us, this would have been a dream come true," he said, recalling the days when he was a lieutenant colonel in the defunct communist country's secret police, the Stasi.
In those days, his department was limited to tapping 40 phones at a time, he recalled. Decide to spy on a new victim and an old one had to be dropped, because of a lack of equipment. He finds breathtaking the idea that the U.S. government receives daily reports on the cellphone usage of millions of Americans and can monitor the Internet traffic of millions more.
"So much information, on so many people," he said.
East Germany's Stasi has long been considered the standard of police state surveillance during the Cold War years, a monitoring regime so vile and so intrusive that agents even noted when their subjects were overheard engaging in sexual intercourse. Against that backdrop, Germans have greeted with disappointment, verging on anger, the news that somewhere in a U.S. government databank are the records of where millions of people were when they made phone calls or what video content they streamed on their computers in the privacy of their homes.
Even Schmidt, 73, who headed one of the more infamous departments in the infamous Stasi, called himself appalled. The dark side to gathering such a broad, seemingly untargeted, amount of information is obvious, he said.
"It is the height of naivete to think that once collected this information won't be used," he said. "This is the nature of secret government organizations. The only way to protect the people's privacy is not to allow the government to collect their information in the first place." ....
Ex-Stasi boss green with envy over NSA's domestic spy powers
For Wolfgang Schmidt, who used to head East Germany's feared spy service, the NSA's reported spy program "would have been a dream come true."
by Charles Cooper June 28, 2013 11:22 AM PDT
"The government can wiretap some of the people all of the time
the government can wiretap all of the people some of the time
the government wants to wiretap all of the people all of the time."
-- with apologies to A. Lincoln

Menwith Hill NSA / GCHQ spy base, Yorkshire, England
www.guardian.co.uk/uk/2013/jun/21/gchq-cables-secret-world-communications-nsa
GCHQ taps fibre-optic cables for secret access to world's communications
Exclusive: British spy agency collects and stores vast quantities of global email messages, Facebook posts, internet histories and calls, and shares them with NSA, latest documents from Edward Snowden reveal
Ewen MacAskill, Julian Borger, Nick Hopkins, Nick Davies and James Ball
The Guardian, Friday 21 June 2013 12.23 EDT
excerpt:
Historically, the spy agencies have intercepted international communications by focusing on microwave towers and satellites. The NSA's intercept station at Menwith Hill in North Yorkshire played a leading role in this. One internal document quotes the head of the NSA, Lieutenant General Keith Alexander, on a visit to Menwith Hill in June 2008, asking: "Why can't we collect all the signals all the time? Sounds like a good summer project for Menwith."
By then, however, satellite interception accounted for only a small part of the network traffic. Most of it now travels on fibre-optic cables, and the UK's position on the western edge of Europe gave it natural access to cables emerging from the Atlantic.
---
note: Menwith has a new wind farm next to it, which ensures the spies will have power if the British power grid has problems as North Sea natural gas dries up. It's now been exactly a century since Peak Coal happened in Britain (1913).
www.truth-out.org/news/item/17459-att-tech-blew-the-whistle-on-nsa-spying-in-2006
AT&T Tech Blew the Whistle on NSA Spying - in 2006
Tuesday, 09 July 2013 09:23
By Jenny Brown, Labor Notes | Interview
Many are shocked by the indiscriminate U.S. government spying revealed by Edward Snowden, the contract employee who blew the whistle on the National Security Agency in June. We shouldn't have been. Signs of this program stretch back more than a decade, and received plenty of media attention in 2006.
Much of that attention was due to revelations by a union AT&T technician in San Francisco, Mark Klein, who noticed and documented suspicious activities at his workplace. He wrote and published a book Wiring Up the Big Brother Machine—And Fighting It detailing his experiences. Labor Notes interviewed him last week about what he found then, and about the new revelations.
You discovered some of the mechanics of NSA spying a decade ago. How did it happen?
I was sitting at my workstation in a small AT&T office in San Francisco in the summer of 2002 when we received an email from higher-ups that a representative of the National Security Agency (NSA) would be coming for an unspecified purpose. He talked to one of the non-union management technicians who worked out of that office and were dispatched for special jobs. We quickly learned that this one tech was being given security clearance by the NSA to work in a "secret room" which was being built at a nearby central office at 611 Folsom St.
As it happened, in 2003 our small office was closed in a "downsizing" and we were transferred to that very office on Folsom St., and by chance my main assignment was to oversee the internet room. In the next few months, I took over from the previous tech, who was retiring, and in the process gathered three critical AT&T engineering documents which revealed how the "secret room" on the sixth floor was tapping into the internet data stream flowing through the seventh floor main room.
Critical to this was a cabinet containing "splitters," which are glass prisms that split the laser light beam that carries the data. Each half of the split carries all the data, effectively making an exact copy of the data, every second of every day. And the wiring documents clearly showed that the copies were being sent to the "secret room."
Part of my job was to wire up circuits to the splitter cabinet, and also troubleshoot problems on those circuits. In fact, while troubleshooting one such problem with a technician in a distant city, I learned they had similar splitters installed in other cities. I was literally wiring up the "big brother machine," and I did not like it.The documents also revealed that they were using a sophisticated, programmable piece of spying gear made by a company called Narus: a Semantic Traffic Analyzer, which, as the name implies can read the content of messages, as well as the addressing information (the from/to part). So essentially the government was getting everything.
I did nothing at that time, but when I retired in mid-2004, I took the documents with me. When the New York Times revealed in December 2005 that President Bush was doing repeated warrantless surveillance on Americans in defiance of the FISA law (Foreign Intelligence Surveillance Act) as well as the Fourth Amendment, I decided to come forward.
What are your thoughts on the newest exposures as a result of Edward Snowden's whistleblowing?
Snowden has revealed a much deeper and broader level of NSA penetration of the internet, the so-called PRISM program, which the documents he released show actually started in 2007 under Bush and expanded under Obama. My revelation had shown the NSA copies data as it flowed across the internet, which gives them a huge amount of everyone's information. But what was missing was your private account data stored on servers by the various companies (Microsoft, Google, Yahoo, Apple, etc.), data which may not be flowing at the moment.
I think NSA whistleblower William Binney, who as a former insider is much more knowledgeable about this (he actually designed the surveillance system before he quit in late 2001 when it was turned against the domestic population) described it precisely. He says the "dragnet" operation I revealed gives them about 80 percent of the information, but the missing piece, the 20 percent, they get from PRISM. Now they have everything, and we are all stripped naked.
PRISM slides - revealed by Edward Snowden

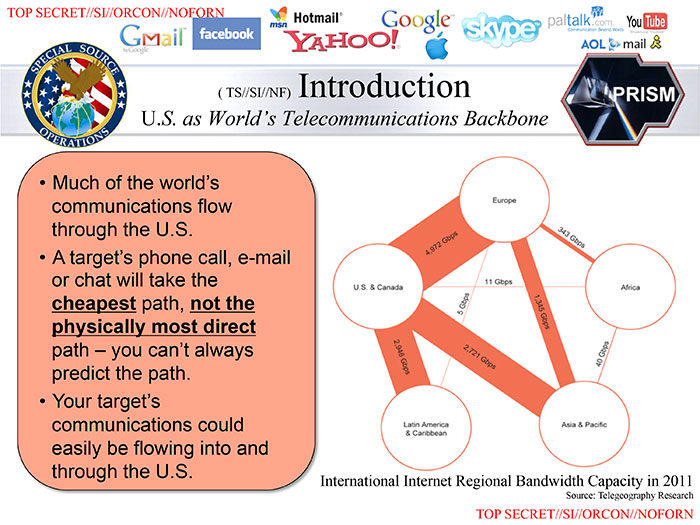
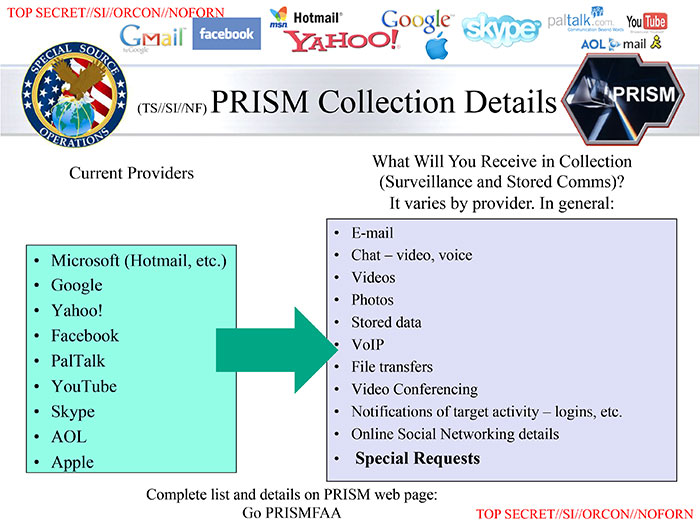
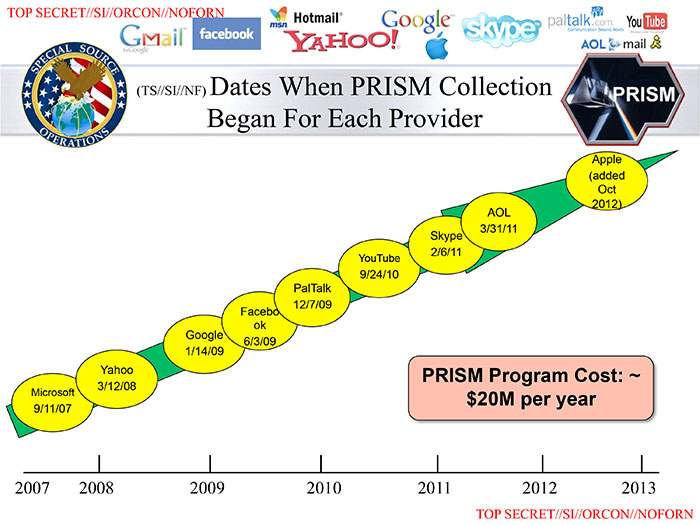
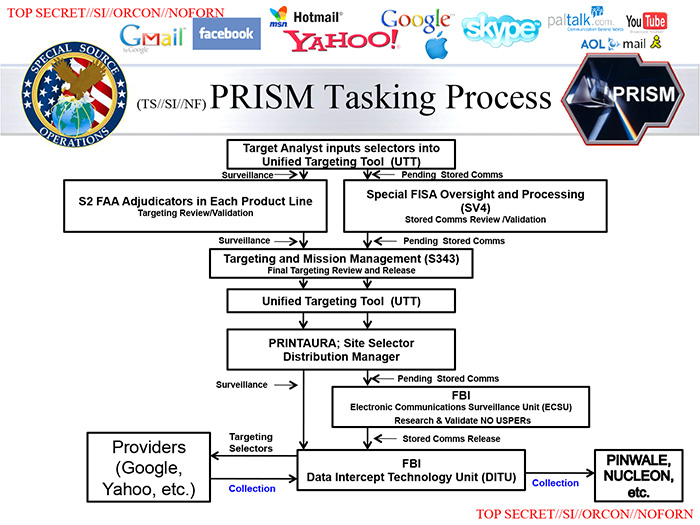
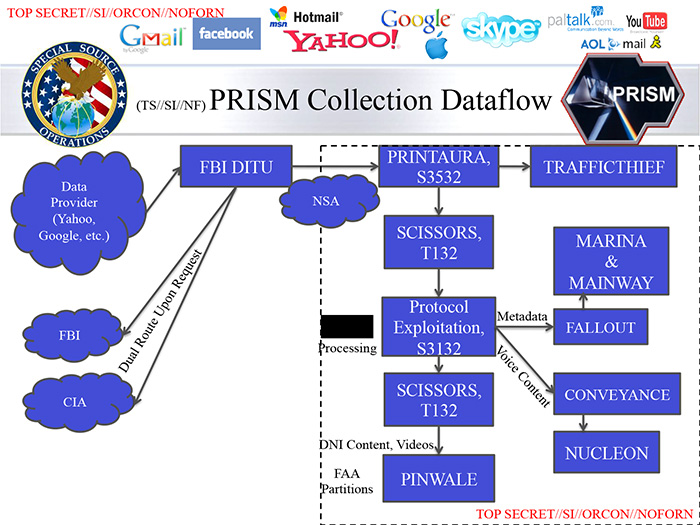

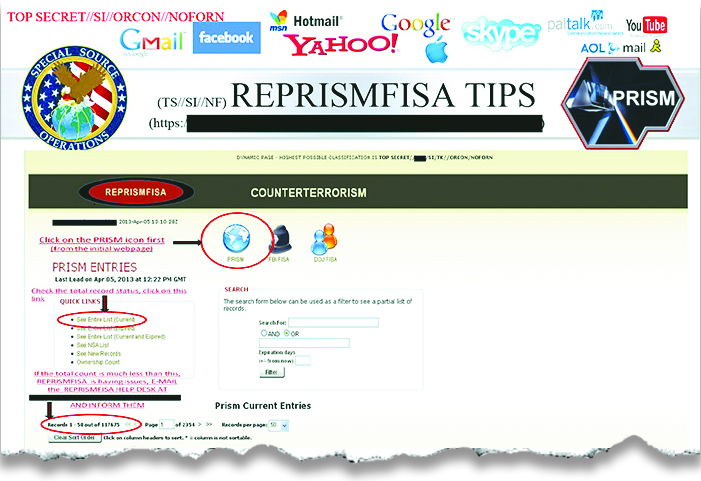
cryptome.org, based in New York City, is one of the best "open source" databases of information related to so-called "intelligence" operations. Here are a few links to their compilations about the No Such Agency:
www.cryptome.org/2013/06/nsa-arch.spy.htm
"Architecture of Oppression" - NSA whistleblower Edward Snowden's term for the surveillance state
Cryptome summary of how their site has documented these abuses
1975 report by the Senate Select Committee on Intelligence Activities, "The National Security Agency and Fourth Amendment Rights": http://cryptome.org/nsa-4th.htm
Unlucky SHAMROCK -- The View From the Other Side http://cryptome.org/nsa-4th-view.htm

from the Church Committee, 1975
www.cryptome.org/nsa-program.htm
State of War: the Secret History of the CIA and the Bush Administration, James
Risen, published 3 January 2006, pp. 42-60.
HPSCI Clashes with NSA On Oversight (1999) http://jya.com/nsa-clash.htm
US Signals Intelligence Directive 18 (1993) http://cryptome.org/nsa-ussid18.htm
http://cryptome.org/nsa-4th-p2.htm
INTELLIGENCE ACTIVITIES -- THE NATIONAL SECURITY AGENCY AND FOURTH AMENDMENT
RIGHTS
THURSDAY, NOVEMBER 6, 1975
U.S. SENATE
SELECT COMMITTEE TO STUDY GOVERNMENTAL OPERATIONS WITH RESPECT TO INTELLIGENCE
ACTIVITIES
http://jya.com/echelon-dc.htm
NEW STATESMAN
12 August 1988
Cover, pages 10-12
Somebody's listening by Duncan Campbell
http://cryptome.org/stoa-atpc.htm
EUROPEAN PARLIAMENT
SCIENTIFIC AND TECHNOLOGICAL OPTIONS ASSESSMENT (STOA)
AN APPRAISAL OF TECHNOLOGIES OF POLITICAL CONTROL
Working document
(Consultation version)
Luxembourg, 6 January 1998
PE 166 499
Directorate General for Research
http://jya.com/nsa-elint.htm
Ramparts, Vol. 11, No. 2, August, 1972, pp. 35-50
U.S. Electronic Espionage: A Memoir
http://jya.com/nsa-40k.htm
Nation Review (AU) 1973
Uncle Sam and his 40,000 snoopers
The following is an interview with a former US operative, now in Australia,
of America's National Security Agency ...
http://jya.com/echelon.htm
EXPOSING THE GLOBAL SURVEILLANCE SYSTEM
by Nicky Hager
http://cryptome.org/echelon2-arch.htm
ECHELON'S ARCHITECT
Echelon now has a big brother. Meet Bruce McIndoe, lead architect for Echelon
II, the 'most productive intelligence program' in history
By Bo Elkjaer and Kenan Seeberg
http://jya.com/echelon2.htm original sources on Echelon
http://cryptome.org/small-call.htm
Our President has chosen to declare himself above the law, a dangerous precedent that could do great harm to our country. However, without substantial effort on the part of you, and I mean you, every person reading this, nothing much is going to happen. The rule of law will continue to decay in our country. Future Presidents will claim even greater extralegal authority, and our nation will fall into despotism. I mean that sincerely. For the sake of yourself, your children and your children's children, you cannot allow this to stand.
http://cryptome.org/sigint-hr-dc.htm
Signals intelligence and human rights
the ECHELON report
Prepared by Duncan Campbell
9 June 2000
(not from cryptome)
The Church Committee report
www.icdc.com/~paulwolf/cointelpro/churchfinalreportIIIe.htm
WARRANTLESS FBI ELECTRONIC SURVEILLANCE
SUPPLEMENTARY DETAILED STAFF REPORTS ON INTELLIGENCE ACTIVITIES AND THE RIGHTS OF AMERICANS
FINAL REPORT
OF THE
SELECT COMMITTEE
TO STUDY GOVERNMENTAL OPERATIONS
WITH RESPECT TO
INTELLIGENCE ACTIVITIES
UNITED STATES SENATE
APRIL 23 (under authority of the order of April 14), 1976